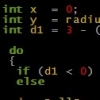
i never thinked about ot so i would like to ask in this case.
lets assume that instead od loading javascript code into a browsers
you download a binary compiled c/asm modules (in the form of
dlls or something like that) such dll should be restricted only to
modify client area of web browser but could use full processor and
gpu abilities
can it be done safe (on windows especially) or there are some basic
problems to do it safe that disqualify this tehnology?